Key Takeaway: Secure Crypto Wallet
Securing your crypto wallet starts with proven, user-friendly tools. Hardware wallets like Ledger, Trezor, Tangem, and SafePal reduce online attack risk. They help keep private keys isolated from malware and phishing traps.
- Protect your seed phrase like cash, and never share it.
- Use strong passwords, and avoid reusing them across services.
- Enable two-factor authentication wherever your wallet supports it.
- Verify links and addresses carefully before sending any funds.
- Keep backups offline, and store them in separate safe places.
Most wallet losses happen due to avoidable mistakes and weak setups. Many beginners trust random apps, fake extensions, or copied websites. Wrong tools can expose seed phrases and drain funds fast. Poor backups can lock you out permanently after phone loss.
I have seen traders lose years of savings in minutes. I suggest starting with simple, trusted security steps today. Proper tools reduce risk and improve daily confidence. This guide reviews reliable options and explains why they matter. It helps you choose tools with clear, honest tradeoffs.
What Is a Crypto Wallet?
A crypto wallet is a digital tool that stores and manages the private keys needed to access, send, and receive cryptocurrencies. It doesn’t hold coins directly but proves ownership on the blockchain, enabling users to securely manage their digital assets. Know more
Understanding Crypto Wallets
Core Concepts: Private Keys, Public Keys, and Seed Phrases
Cryptocurrency gives you full control over your money—but that control comes with full responsibility. Unlike traditional banks, there is no customer support to recover lost funds if your wallet is compromised. Understanding and protecting the core components of a crypto wallet is essential to staying safe.
The three most important concepts to master are private keys, public keys, and seed phrases.
1. Private Keys: Your Ultimate Access Code
A private key is a long, cryptographic string that proves ownership of your cryptocurrency. Whoever controls the private key controls the funds.
Why Private Keys Matter
- They authorize transactions from your wallet
- They must remain secret at all times
- If stolen or exposed, your crypto can be drained instantly
How to Secure Your Private Keys
- Never share them with anyone—no legitimate service will ask for them
- Avoid storing them digitally (screenshots, cloud storage, emails)
- Use hardware wallets to keep private keys offline
- If using a software wallet, protect it with a strong password and device security
2. Public Keys: Your Wallet Address
A public key is derived from your private key and is used to receive cryptocurrency. It’s often converted into a wallet address that you can safely share.
What Public Keys Are Used For
- Receiving funds
- Verifying transaction ownership
- Allowing others to send crypto to your wallet
Security Considerations
- Public keys are safe to share, but:
- Reusing the same address can reduce privacy
- Anyone can view transactions associated with it on the blockchain
Best Practices
- Use new addresses when possible to enhance privacy
- Share addresses carefully to avoid scams (check for copy-paste malware)
- Double-check addresses before sending or receiving funds
3. Seed Phrases: Your Wallet Backup
A seed phrase (also called a recovery phrase) is a list of 12–24 words that can restore your wallet and all associated funds.
Why Seed Phrases Are Critical
- They can recreate your private keys
- Losing them means permanent loss of access
- Anyone with the seed phrase can control your wallet
How to Secure Your Seed Phrase
- Write it down on paper—never store it digitally
- Store copies in secure, separate locations
- Consider metal backups to protect against fire or water damage
- Never enter it on websites or share it with anyone
Types of Crypto Wallets
Understanding the types of crypto wallets is a key step in learning how to secure my crypto wallet. Each wallet type is built for a different use case. Some focus on fast access, while others focus on strong protection. New users often choose convenience first, but long-term safety should guide the decision. A smart choice depends on how often you trade, how much crypto you hold, and how comfortable you are with managing security.
Crypto wallets are mainly grouped by whether they stay online or offline. Online wallets are easier to use but face more risks. Offline wallets reduce exposure to hacks and phishing attacks. Over time, many users shift from simple wallets to more secure options as their assets grow.
- Software Wallets: These wallets are apps on mobile phones or computers. They are suitable for daily transactions and small balances. Security depends on device safety and password strength.
- Web Wallets: These wallets work through browsers. They offer quick access from anywhere. The downside is reliance on third-party platforms.
- Hardware Wallets: These are physical devices that store private keys offline. They are trusted for long-term storage and higher-value crypto.
- Paper Wallets: These store keys on paper. They avoid online risks but need careful physical storage.
How Wallets Work
Understanding how wallets work is essential when learning how to secure my crypto wallet. A crypto wallet does not store coins directly. Instead, it stores private keys. These keys prove ownership and allow access to your funds on the blockchain. If someone gets your private key, they control your crypto. That is why wallet security matters more than the device itself.
Every wallet interacts with the blockchain in a simple way. When you send crypto, the wallet signs a transaction using your private key. The blockchain then verifies it and updates the balance. When you receive crypto, the wallet simply shows that new balance linked to your public address.
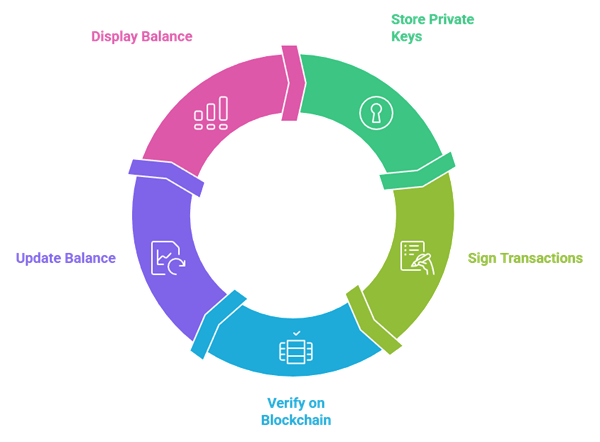
- Private and public keys: The public key works like an address. You can share it safely. The private key must stay secret at all times.
- Transaction signing: Wallets sign transactions locally. This prevents private keys from being exposed during transfers.
- Wallet interface: The wallet app helps you view balances, send funds, and receive crypto easily.
- Blockchain connection: Wallets read data from the blockchain to show accurate balances.
Common Crypto Wallet Security Threats
- Phishing attacks are the biggest threat today. Fake emails and websites steal private keys or recovery phrases.
- Malware infections can track keystrokes or change wallet addresses during transactions.
- Public Wi-Fi networks expose wallet activity to hackers using data interception methods.
- Weak passwords make wallets easy targets for brute force attacks.
- Reused credentials increase risk if one platform gets compromised.
- Lost or stolen devices can lead to permanent fund loss without proper backups.
- Fake wallet apps often appear in app stores and trick new users.
- Smart contract exploits mainly affect DeFi wallets and connected platforms.
Essential Steps to Secure Your Crypto Wallet
Step 1: Choose the right wallet type: Use a hardware wallet for large holdings. Software wallets suit daily use but carry higher risk.
Step 2: Protect your recovery phrase: Write it on paper and store it offline. Never save it on cloud apps or screenshots.
Step 3: Use strong and unique passwords: Create long passwords and avoid reuse across platforms.
Step 4: Enable two factor authentication: This adds an extra layer even if your password is exposed.
Step 5: Keep software updated: Updates fix security gaps and reduce attack risks.
Step 6: Avoid public networks: Public Wi-Fi makes wallets easier to target.
Best Practices for Daily Crypto Wallet Use
- Always lock your wallet app when not in use to prevent quick access by others.
- Check wallet addresses carefully before sending crypto since mistakes cannot be reversed.
- Use small balances for daily transactions and keep long term funds in cold storage.
- Avoid clicking unknown links related to crypto offers or wallet updates.
- Log out of connected dApps after use to reduce exposure.
- Keep devices clean from malware by installing trusted security updates.
- Do not share screens when your wallet is open during calls or streams.
- In my experience, daily discipline prevents most losses.
- I treat my wallet like cash and stay alert at all times.
Advanced Security Measures
- Use multi signature wallets for high value funds: They require multiple approvals before any transfer. This limits damage if one key is compromised.
- Rely on hardware wallets for long term storage: Private keys stay offline and away from online threats. This makes them safer than software wallets.
- Add a hidden passphrase to your recovery phrase: It creates an extra lock that protects funds even if the main phrase is exposed.
- Enable address whitelisting: Crypto can only be sent to approved addresses. This helps avoid errors and malicious redirection.
- Use a separate device for crypto activity: A clean device reduces risks from malware and unsafe downloads.
- Turn on time delay for withdrawals: Delays allow you to react if a transaction looks suspicious.
- Review wallet and app permissions regularly: Remove old or unused connections to lower attack points.
I follow layered security because no single tool is enough. My goal is strong protection without hurting daily usability.
Recognizing and Avoiding Crypto Scams
Crypto scams are one of the biggest risks when learning how to secure my crypto wallet. Most scams follow clear patterns. Fake giveaways promise fast returns. Phishing emails copy real exchanges and ask for keys. Impersonators pose as support on social media. If someone asks for your private key, it is a scam. No exception.
I always check the source before clicking any link. Real platforms never rush you. Scammers push fear or excitement. That pressure is a warning sign. Compare website URLs carefully. Small spelling changes matter. Use bookmarks for trusted sites.
Another common trick is fake wallet apps. Download only from official stores. Read recent reviews and check update dates. Cold messages offering help are risky.
Strong habits reduce exposure. Use two factor authentication. Verify transactions before approval. Staying calm and skeptical protects assets better than any tool. Education and patience remain essential for long term crypto safety.
What to Do If Compromised
Discovering that your crypto wallet has been compromised can be alarming, but acting quickly and correctly can help minimize losses and prevent further damage. Follow these steps immediately if you suspect unauthorized access to your wallet.
- Stop Using the Wallet & Move Funds
- Stop all activity on the compromised wallet.
- Transfer any remaining funds to a new, secure wallet with a fresh seed phrase using a clean device.
- Create a New Wallet
- Generate a completely new wallet from a trusted provider.
- Securely back up the new seed phrase offline.
- Secure Your Devices
- Scan your computer and phone for malware.
- Remove suspicious apps or browser extensions.
- Update your operating system and wallet software.
- Change Passwords & Revoke Access
- Change passwords for emails, exchanges, and related accounts.
- Enable 2FA.
- Revoke permissions from unknown or suspicious dApps.
Conclusion
A compromised crypto wallet can be stressful, but quick and decisive action can limit the damage. By immediately stopping wallet activity, moving funds to a secure new wallet, securing your devices, and tightening access controls, you can regain control and protect your assets. Most importantly, treat wallet security as an ongoing practice—regular reviews and strong security habits are the best defense against future attacks.
Frequently Asked Questions (FAQ)
Is it safe to store crypto on exchanges?
Storing crypto on exchanges is convenient but not fully safe. Exchanges control private keys, making funds vulnerable to hacks, freezes, or insolvency. Use exchanges only for trading. For long-term storage, move assets to self-custody wallets (hardware or reputable software) where you control keys and reduce third-party risk. Enable strong security features if you must keep funds there.
Can I recover crypto if I lose my private key?
Crypto recovery is generally impossible if you lose your private key or recovery phrase. Blockchains are decentralized, with no password reset or authority. If you secured a backup seed phrase, you can restore access. Without it, funds are permanently inaccessible, highlighting the importance of secure, offline backups stored in multiple safe physical locations.
How often should I update my wallet security?
Wallet security should be reviewed regularly and updated whenever risks change. Check settings every 3–6 months, update software promptly, rotate passwords, and re-verify backups. Immediately update security after device changes, phishing attempts, or new threats. Consistent hygiene reduces attack surfaces and protects long-term holdings. Use hardware wallets and enable multi-factor authentication where available.




